“Cloud-Based Security Options for Ex-AT&T Users” sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail with a focus on protecting your online security. As technology advances, ensuring the safety of your digital information becomes paramount, especially for those transitioning from AT&T services.
Let's explore the world of cloud-based security options and how they can benefit ex-AT&T users.
Introduction to Cloud-Based Security
Cloud-based security refers to the practice of protecting data, applications, and infrastructure in the cloud environment. It utilizes cloud computing resources to deliver security services, offering a scalable and cost-effective solution for safeguarding digital assets.
For ex-AT&T users, cloud-based security is crucial in ensuring the protection of sensitive information and maintaining privacy in an increasingly digital world. With the rise of cyber threats and data breaches, having robust security measures in place is essential for safeguarding personal and business data.
Benefits of Cloud-Based Security for Ex-AT&T Users
Implementing cloud-based security options can bring several advantages to ex-AT&T users:
- Enhanced Security Measures: Cloud-based security solutions offer advanced threat detection and prevention capabilities, helping users defend against cyber attacks and unauthorized access.
- Scalability and Flexibility: Users can easily scale their security measures based on changing needs and requirements, without the need for extensive hardware upgrades.
- Cost-Effectiveness: Cloud-based security eliminates the need for investing in costly infrastructure and maintenance, providing a more affordable security solution for ex-AT&T users.
- Remote Accessibility: Users can access and manage their security measures from anywhere, providing greater convenience and control over their digital protection.
Types of Cloud-Based Security Options
When it comes to cloud-based security options, there are several types available to choose from. Let's explore some of the most common ones and compare them for ex-AT&T users.
1. Cloud-Based Antivirus Solutions
Cloud-based antivirus solutions offer real-time protection against malware, viruses, and other online threats. These solutions rely on cloud servers to continuously update and scan for new threats, providing a more proactive approach to security.
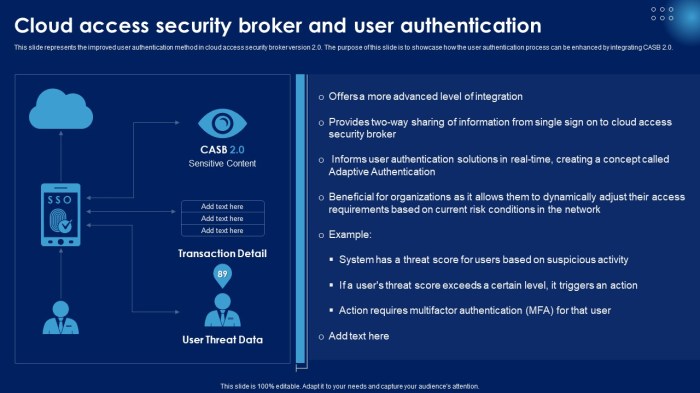
2. Cloud Access Security Brokers (CASBs)
CASBs act as intermediaries between users and cloud service providers, ensuring data security, compliance, and governance in cloud applications. They provide visibility and control over data shared in the cloud, making them essential for ex-AT&T users concerned about data privacy.
3. Cloud-Based Web Application Firewalls (WAFs)
WAFs protect web applications from cyber attacks by monitoring and filtering HTTP traffic between a web application and the Internet. They help prevent common web vulnerabilities such as SQL injection and cross-site scripting, offering an added layer of security for ex-AT&T users accessing cloud-based applications.
4. Cloud Identity and Access Management (IAM)
Cloud IAM solutions manage user identities, roles, and access permissions within cloud environments. They help ex-AT&T users control who has access to which resources, reducing the risk of unauthorized access and data breaches.
Popular Cloud-Based Security Providers and Offerings
Microsoft Azure
Offers a range of security services including Azure Security Center for threat protection and Azure Active Directory for identity and access management.
Amazon Web Services (AWS)
Provides services like AWS Identity and Access Management (IAM) and AWS WAF for web application security.
Google Cloud Platform
Offers Google Cloud Identity for centralized identity management and Google Cloud Armor for DDoS protection.These are just a few examples of popular cloud-based security providers and their offerings that ex-AT&T users can consider to enhance their online security.
Considerations for Ex-AT&T Users
Ex-AT&T users transitioning to cloud-based security options need to carefully consider their specific security needs and challenges in order to seamlessly integrate these solutions into their existing systems. By understanding the factors involved in choosing the right cloud-based security option, ex-AT&T users can effectively enhance their cybersecurity measures.
Identifying Specific Security Needs and Challenges
Ex-AT&T users may have unique security needs and challenges due to their previous telecom provider's infrastructure. Some key considerations for ex-AT&T users include:
- The need for secure data transmission and storage to protect sensitive information.
- Addressing potential vulnerabilities that may arise during the transition to a new security system.
- Ensuring compatibility with existing AT&T systems and applications for a smooth integration process.
Seamless Integration of Cloud-Based Security
Integrating cloud-based security seamlessly into existing systems requires careful planning and execution. Ex-AT&T users can achieve this by:
- Conducting a thorough assessment of their current security infrastructure to identify gaps and areas for improvement.
- Collaborating with security experts to customize cloud-based solutions that meet their specific needs and requirements.
- Training employees on the new security protocols and systems to ensure proper implementation and utilization.
Factors to Consider in Choosing a Cloud-Based Security Option
When selecting a cloud-based security option, ex-AT&T users should take into account various factors to make an informed decision. These factors include:
- Scalability and flexibility of the security solution to accommodate future growth and changes in security needs.
- Compliance with industry regulations and standards to ensure data protection and legal adherence.
- Cost-effectiveness and ROI analysis to determine the long-term value and benefits of the chosen security option.
Implementation and Best Practices
Implementing cloud-based security solutions for ex-AT&T users requires careful planning and execution to ensure a smooth transition. Here are the steps to follow and best practices to consider:
Steps to Implement Cloud-Based Security Solutions
- Evaluate your security needs and identify the most suitable cloud-based security options based on your requirements.
- Choose a reliable cloud service provider with a good track record in security and compliance.
- Develop a migration plan to move your data and applications to the cloud securely.
- Configure the cloud-based security solutions according to best practices and industry standards.
- Test the security measures thoroughly before fully deploying them to ensure they work effectively.
Best Practices for Configuring and Optimizing Cloud-Based Security
- Enable multi-factor authentication for an added layer of security.
- Regularly update and patch your cloud-based security solutions to protect against new threats.
- Implement encryption for sensitive data to prevent unauthorized access.
- Monitor user activity and access permissions to detect any suspicious behavior.
- Train employees on security best practices to minimize human error.
Tips on Monitoring, Managing, and Updating Cloud-Based Security
- Use a centralized dashboard to monitor security events and respond to incidents promptly.
- Regularly review security logs and reports to identify any anomalies or potential threats.
- Perform regular security audits to assess the effectiveness of your cloud-based security measures.
- Stay informed about the latest security trends and updates in the cloud computing industry to adapt your security strategy accordingly.
Closure

In conclusion, "Cloud-Based Security Options for Ex-AT&T Users" delves into the realm of online security, shedding light on the importance of protecting your data in today's digital age. By embracing cloud-based security solutions, ex-AT&T users can navigate the online landscape with confidence and peace of mind.
Stay informed, stay secure.
Helpful Answers
What is cloud-based security?
Cloud-based security refers to the use of cloud computing technology to protect data, applications, and other digital assets from cyber threats.
Why is cloud-based security important for ex-AT&T users?
Ex-AT&T users need robust security measures to safeguard their data during the transition from AT&T services. Cloud-based security offers a reliable solution to protect their digital presence.
How can ex-AT&T users integrate cloud-based security into their systems?
Ex-AT&T users can seamlessly integrate cloud-based security by carefully selecting compatible solutions and following best practices for implementation.
What factors should ex-AT&T users consider when choosing a cloud-based security option?
Ex-AT&T users should consider factors such as data encryption, scalability, and ease of integration when selecting a cloud-based security option.
What are the best practices for configuring and optimizing cloud-based security?
Best practices include regular updates, strong authentication measures, data backups, and monitoring for any suspicious activities.











